GCP App Engine via Cloud Flare – Step by Step
Usually, it is wise to protect your application against DDOS, XSS and SQL injections and so on. Unfortunately, at this moment it is impossible to use Google Cloud Armor with Google App Engine. The one solution can use Azure Application Gateway with WAF or Cloud Flare. How to configure Cloud Flare with App Engine – Step by Step:
- As usual, you must delegate DNS zone to Cloud Flare – it is easy to process after you register in Clod Flare.
- On Google Cloud Console – go to App Engine panel, Setting and Custom domains and you must add Custom Doman.
- You need to Verify a new domain, by adding the TXT record to your DNS settings. You do it in Cloud Flare. Please remember if you are adding it to the subdomain e.g. cc.wiadk.pl, you need to add TXT record to subdomain cc.wiadki.pl.
If you have a problem with it you can switch to add CNAME record. That’s works better for me. -
After Verifying domain Google will create an SSL certificate for your domain for it, but it not works with Cloud Flare at this moment, so you need to disable SSL security like here:
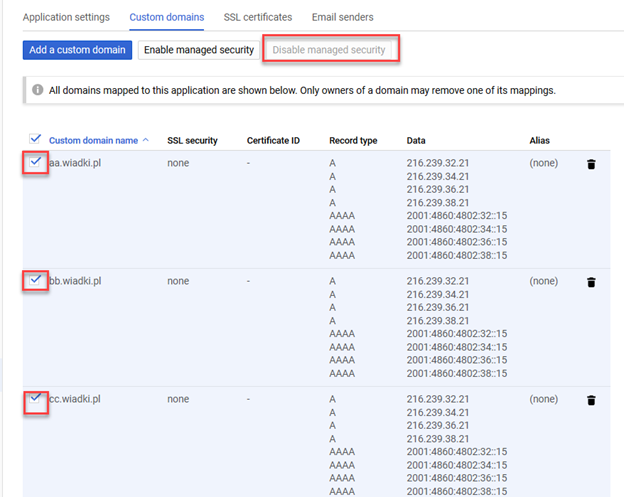
-
Now you can add A records in Cloud Flare:

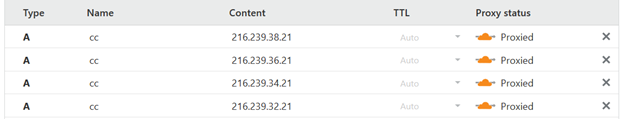
You can also add IPV6 addresses.
-
During my test, Full End-To-end encryption didn’t work for me so we need to go to SSL/TLS settings and select flexible mode – like here:
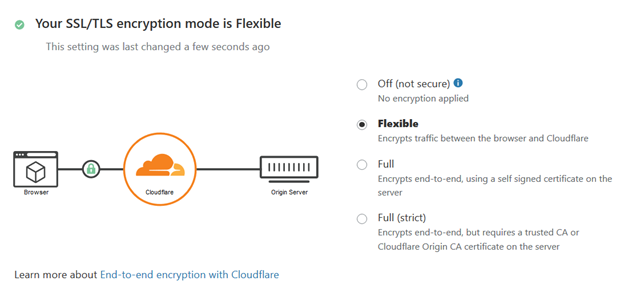
If you want to use Flexible mode only for one subdomain you can do it by using Pages Rules like here:
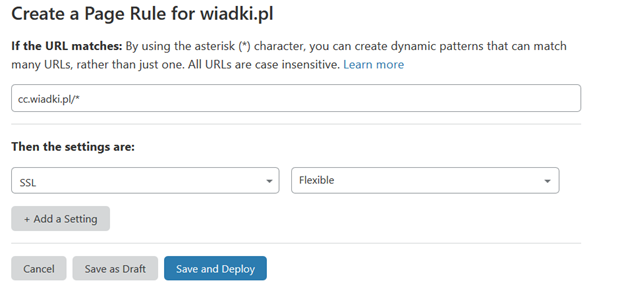
In this way, only cc.wiadki.pl will be without end-to-end encryption.
-
You can also use option Always use HTTPS to redirect from HTTP to HTTPS using Pages Rules like here:
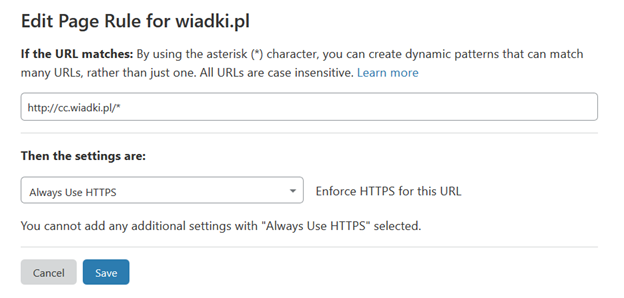
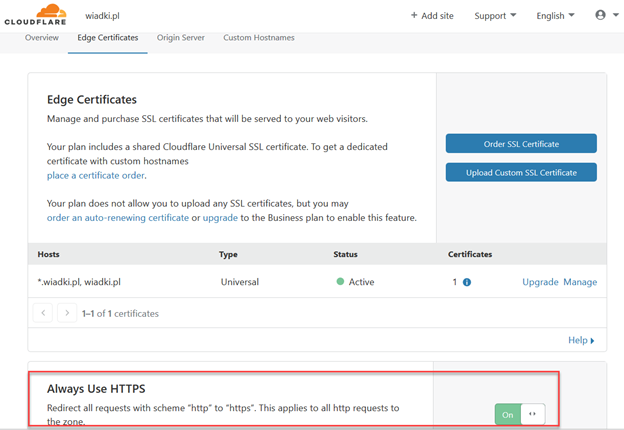
Or for all entries in your domain in SSL/TLS – Edge Certificates Settings:
So for some time you can visit and test how this App Engine page works through Cloud Flare proxy:
After you enable Cloud Flare for App Engine please remember that App Engine still will be available using *.appspot.com address so please protect it using Client Certificate, Reverse Connection or at least IP restriction https://www.cloudflare.com/ips/.
More info:
https://support.cloudflare.com/hc/en-us/articles/200170166-Best-Practices-DDoS-preventative-measures