Polityka haseł jaka powinna być / Password Policy – na podstawie / based on Azure Identity Secure Score
W czasie Ignite 2018 Microsoft wprowadził Identity Secure Score dostępną w panelu Azure Active Directory. Oprogramowanie informuje nas ile punktów od 1 do 248 zebraliśmy, za prawidłową i bezpieczną konfigurację usług dostępnych w chmurze Microsoft. Dodatkowo widzimy, ile i za co dodatkowych punktów możemy zdobyć. Wszyscy lubimy się porównywać, dlatego też mamy informacje, czy nasz wynik jest powyżej średniej, czy poniżej w sektorze gospodarki.
Poniżej screen wraz z kilkoma wskazówkami dotyczącymi ulepszeń. Po kliknięciu w każde z nich dostajemy dokładną informację co powinniśmy wykonać.
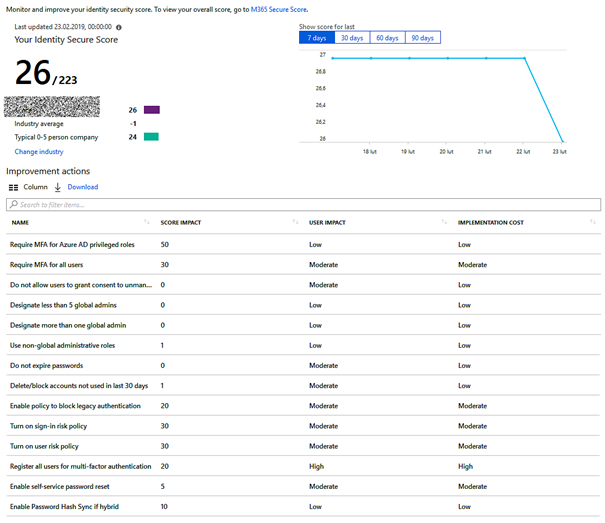
Często dyskutujemy, jak często powinniśmy zmieniać hasła, oraz czy wymuszać je polityką – tutaj wyjaśnienia Microsoft:
Do not expire passwords – Research has found that when periodic password resets are enforced, passwords become less secure. Users tend to pick a weaker password and vary it slightly for each reset. If a user creates a strong password (long, complex and without any pragmatic words present) it should remain just as strong in 60 days as it is today. It is Microsoft’s official security position to not expire passwords periodically without a specific reason. Your current policy is set to require a password reset every 999 days.
What am I about to change? – Under Security & privacy, edit the Password Policy to never let passwords expire. You must be a global admin to edit the password policy.
How will it affect my users? – Your users will no longer need to periodically create new passwords.
Oczywiście wśród zaleceń mamy również zlecenia do włączenia MFA.
Następna polityka to:
Delete/block accounts not used in last 30 days – Deleting or blocking accounts that haven’t been used in the last 30 days, after checking with owners, helps prevent unauthorized use of inactive accounts. These accounts can be targets for attackers who are looking to find ways to access your data without being noticed.
What am I about to change? – Clicking the button below will take you to GitHub where you can download a Powershell script to look up the users who have not logged in for the last 90 days.
Jako odpowiedź na poniższy wpis tutaj link do źródła – polecam zapoznać się (THX- John Flores).
During Ignite 2018 Microsoft introduced Identity Secure Score available in the Azure Active Directory panel. Functionality informs us how many points from 1 to 248 we collected for the correct and safe configuration of services available in the Microsoft cloud. In addition, we see how much and for what we can get additional points. We all like to compare, that’s why we have information if our result is above or below the average.
Below the screen with some tips for improvements. After clicking on each of them, we get the exact information what should we do.
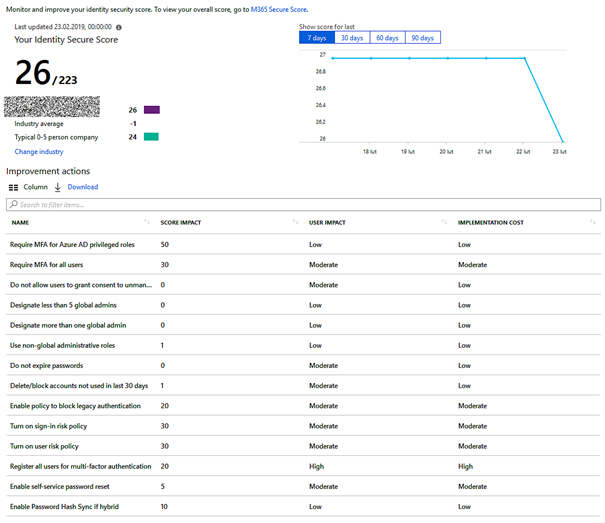
We often discuss how often we should change passwords and whether to force them through GPO or similar- here Microsoft’s explanations:
Do not expire passwords – Research has found that when periodic password resets are enforced, passwords become less secure. Users tend to pick a weaker password and vary it for each reset. If a user creates a strong password (long, complex and without any pragmatic words present) it should remain just like today. It is Microsoft’s official security position. Your current policy is set to require a reset every 999 days.
What am I about to change? – Under Security & privacy, edit the passwords expire. You must be the global admin to edit the password policy.
How will it affect my users? – Your users will need to periodically create new passwords.
Of course, among the recommendations we also have orders to include MFA.
The next policy is:
Delete/block accounts not used in last 30 days – Deleting or blocking accounts that haven’t been used in the last 30 days, after checking with owners, helps prevent unauthorized use of inactive accounts. These accounts can be targets for attackers who are looking to find ways to access your data without being noticed.
What am I about to change? – Clicking the button below will take you to GitHub where you can download a Powershell script to look up the users who have not logged in for the last 90 days.
Here is a MS sorce document (THX- John Flores).