Audit what Operating System is trying to run
Sometimes we need to know what application is doing in our operating system. Some scenario when we need it:
- We run installer to install application and track what installer trying to launch. I used it to find all components during containerization third party application.
- I would like to know what exactly is doing during enabling Azure Disk Encryption.
How to do it?
- Download – https://download.sysinternals.com/files/Sysmon.zip
- Unzip it
- Install using:
sysmon.exe -accepteula –i –h md5,sha256 –n
Sysmon register all network connection and processes that launch in Applications and Services Logs/Microsoft/Widows/Sysmon
- Alternatively we can do it without installing any application – just run gpedit.msc and configure Audit Process Creation:
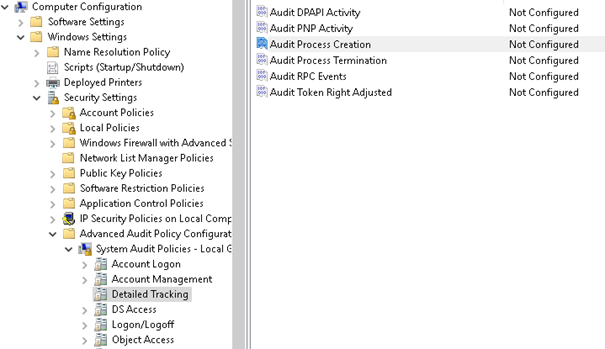
- But it is not all add Include command line in process creation events
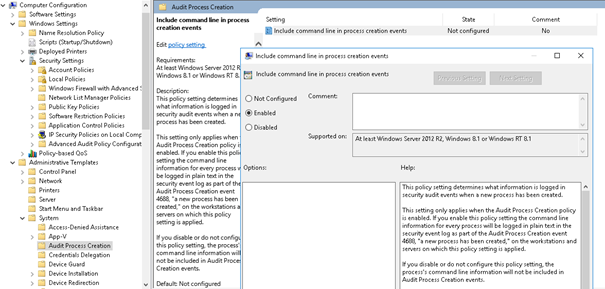
After that issue gpupdate /force
Process Creation Events will go to the Security log.
- Clear in Event Viewer Security log and Sysmon log – you can also delete all logs issuing:
wevtutil el | Foreach-Object {wevtutil cl “$_”}
- Install application that you can minotor
- Export Security and Sysmon log to csv
- Using Notepad++ search for “Process Command Line”. It returns all commands that was issued by the installator.
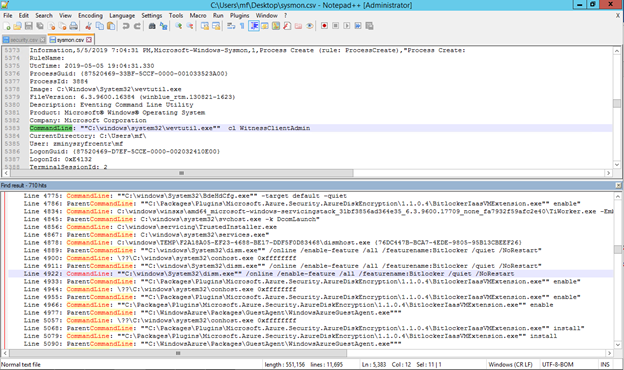
You can also view 5 last events in every log issuing:
Get-WinEvent -ListLog * -EA silentlycontinue | where-object { $_.recordcount -AND $_.lastwritetime -gt [datetime]::today} | foreach-object { get-winevent -LogName $_.logname -MaxEvents 5 } | Format-Table TimeCreated, ID, ProviderName, Message -AutoSize –Wrap
Consider using  and
and  in Azure VM blade.
in Azure VM blade.
Other software that can be helpful:
Folder Changes View: https://www.nirsoft.net/utils/folder_changes_view.html
Registry Changes View: https://www.nirsoft.net/utils/registry_changes_view.html