Azure Disk Encryption – Troubleshooting
Azure Disk Encryption technology basis on Windows BitLocker technology– of course only for Windows VMs. Key for BitLocker is stored in Key Vault. Encryption Agent is responsible for transfer key from Key Vault to VM. We have two version old one that use Azure Active Directory (https://docs.microsoft.com/pl-pl/azure/security/azure-security-disk-encryption-prerequisites-aad) and new one without this (https://docs.microsoft.com/pl-pl/azure/security/azure-security-disk-encryption-windows).
AAD version – AzureDiskEncryption version 1.*, without AAD extension 2.*
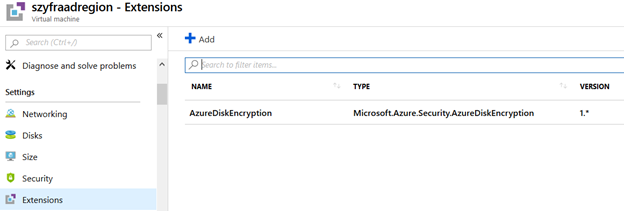
When to use this manual:
- When we use Azure Disc Encryption, before we move VM form one subscription to another we need to suspend BitLocker. Even if we do it and we would like to enable encryption again we need to do it use this procedure
-
When we enable Azure Disk Encryption (old AAD version) and we receive something like this:
Provisioning state Provisioning failed. The Key Vault https:… is located in location EastUS2, which is different from the location of the VM, eastus.. KeyVaultAndVMInDifferentRegions
- During updating Azure Disk Encryption AAD version to Key Vault only (AzureDiskEncryption 1.* to 2.*) – unsupported
- In some scenario after restoring from backup.
- To disable Azure Encryption Disk functionality.
- AzureDiskEncryption Extension – Provisioning failed
-
If we see this error:
What we need to do after checking logs C:\WindowsAzure\Logs\Plugins\Microsoft.Azure.Security.AzureDiskEncryption with no-idea what to do next:
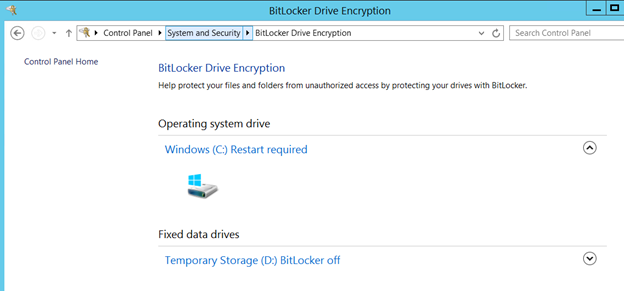
- Suspend Encryption on VM:
Suspend-BitLocker -MountPoint “C:” -RebootCount 0
You can check status issuing:
manage-bde -status
Save numerical recovery password – it can be helpful in any case of problems.
- Try to disable Encryption on Azure:
$VMName = ‘szyfraadregion’
$VMRGName = ‘szyfr_aad_region’
Disable-AzVMDiskEncryption -ResourceGroupName $VMRGName -VMName $VMName
and
Remove-AzVMDiskEncryptionExtension -ResourceGroupName $VMRGName -VMName $VMName
- Try to disable encryption on disks OS and data disks:
$RG=$VMRGName
(get-azurermvm -ResourceGroupName $VMRGName -Name $vmname).StorageProfile.OsDisk
$diskName=((get-azurermvm -ResourceGroupName $RG -Name $vmname).StorageProfile.OsDisk.Name)
$disk = Get-AzureRmDisk -ResourceGroupName $RG -DiskName $diskName
$disk.EncryptionSettings.Enabled = $false
$disk.EncryptionSettings.DiskEncryptionKey = $null
$disk.EncryptionSettings.KeyEncryptionKey = $null
$disk | Update-AzureRmDisk
(get-azurermvm -ResourceGroupName $VMRGName -Name $vmname).StorageProfile.DataDisks #Proceed for every disk
$diskName=((get-azurermvm -ResourceGroupName $RG -Name $vmname).StorageProfile.DataDisks.Name)
$disk = Get-AzureRmDisk -ResourceGroupName $RG -DiskName $diskName
$disk.EncryptionSettings.Enabled = $false
$disk.EncryptionSettings.DiskEncryptionKey = $null
$disk.EncryptionSettings.KeyEncryptionKey = $null
$disk | Update-AzureRmDisk
- Now we need to recreate VM (we cannot usually disable encryption if there is any error) – just Export template – it usually not exports Disk Encryption
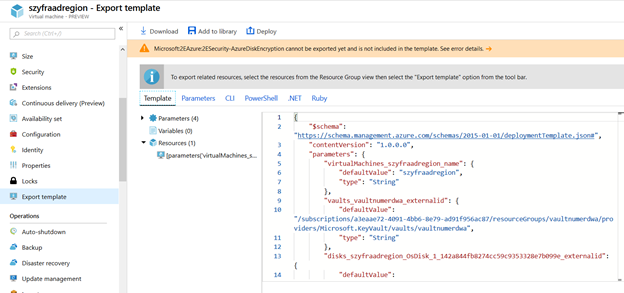
- Delete Only VM – disk networks and rest resources will not be deleted (ensure that VM is deleted – wait a while):
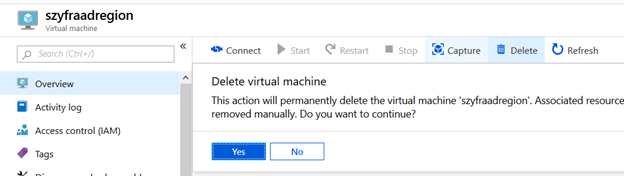
-
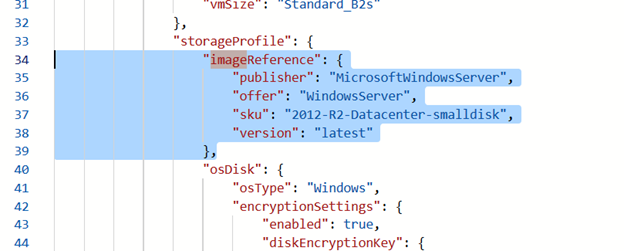
Recreate VM (Template Deployment – Build your own template in the editor) – in template paste content from point 4 and remove some thins (if we restore from backup probably we will have less things to remove):

- Remove OsProfile
- Remove Image Preference
- Remove Disk Size
- Change FromImage to Attach
- Remove Encryption

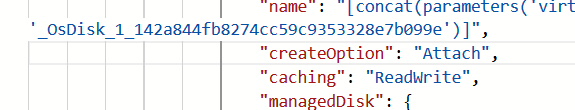
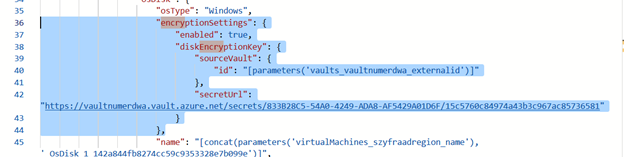
Remove marked items.
- Create VM from template – use the same Resource Grout that we deleted VM.
-
Log to the VM and Disable Encryption:
Now we have disabled Azure Encryption Disk functionality.
You can enable encryption again -please remember that you should use the same version that was use before (AAD or without AAD). Please also remember that in AAD encryption Key vault has to be in the same region as VM.
Azure Disk Encryption with AAD:
$aadClientSecret = “EnableAADEncryptionPa#!@Komplicated”
$aadClientSecretSec = ConvertTo-SecureString -String $aadClientSecret -AsPlainText -Force
$azureAdApplication = New-AzADApplication -DisplayName “DiskEncryptAAD8” -HomePage “https://DiskEncryptAAD8” -IdentifierUris “https://DiskEncryptAAD8” -Password $aadClientSecretSec
$servicePrincipal = New-AzADServicePrincipal –ApplicationId $azureAdApplication.ApplicationId
$keyVaultName = ‘keycentral’
$aadClientID = $azureAdApplication.ApplicationId
$KVRGname = ‘keycentral’
Set-AzKeyVaultAccessPolicy -VaultName $keyVaultName -ServicePrincipalName $aadClientID -PermissionsToKeys ‘WrapKey’ -PermissionsToSecrets ‘Set’ -ResourceGroupName $KVRGname
Set-AzKeyVaultAccessPolicy -VaultName $keyVaultName -ResourceGroupName $KVRGname -EnabledForDiskEncryption
$KeyVault = Get-AzKeyVault -VaultName $KeyVaultName -ResourceGroupName $KVRGname
$DiskEncryptionKeyVaultUrl = $KeyVault.VaultUri
$KeyVaultResourceId = $KeyVault.ResourceId
$sequenceVersion = [Guid]::NewGuid();
Set-AzVMDiskEncryptionExtension -ResourceGroupName $VMRGname -VMName $vmName -AadClientID $aadClientID -AadClientSecret $aadClientSecret -DiskEncryptionKeyVaultUrl $diskEncryptionKeyVaultUrl -DiskEncryptionKeyVaultId $KeyVaultResourceId -VolumeType ‘all’ –SequenceVersion $sequenceVersion;
There will be VM restart.
Without AAD:
$KVRGname = ‘Key_Vault_Name’;
$VMRGName = $RG #Key_Vault_resourceGroup
$KeyVaultName = ‘key_vault;
$KeyVault = Get-AzKeyVault -VaultName $KeyVaultName -ResourceGroupName $KVRGname
$diskEncryptionKeyVaultUrl = $KeyVault.VaultUri;
$KeyVaultResourceId = $KeyVault.ResourceId;
Set-AzVMDiskEncryptionExtension -ResourceGroupName $VMRGname -VMName
$vmName -DiskEncryptionKeyVaultUrl $diskEncryptionKeyVaultUrl -DiskEncryptionKeyVaultId $KeyVaultResourceId;
There will be VM restart.
If we change from AAD version 1.0 to version without 2.0 just before last point on the VM we need to uninstall Agent and clean configuration – This is not supported scenario, but you can read about this here.
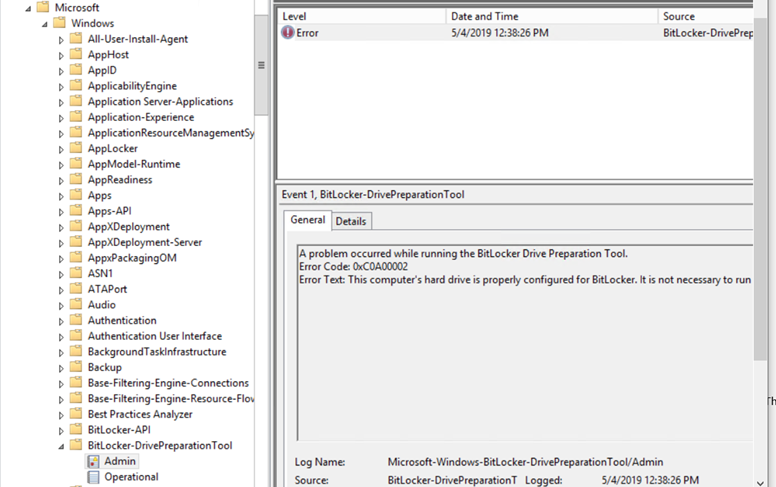
Please always remember that we can check BitLocker status using:
manage-bde -status
or we can also check Event Viewer: