The security problem of the mapping file structure of Azure Web App and other IIS APP – part 2.
Previously I showed you the method of preventing mapping of the file structure of your WebApp based on 404 and 403 response codes. The disadvantage of runAllManagedModulesForAllRequests=”true” method is that it must be handled by application code.
The main problem is that these requests 403 and 404 are server not by IIS from WebApp, but by Load Balancer… So, if we cannot do it in that way, let’s try to use a Web Application Firewall for that. In Azure, we can utilize for that Web Application Firewall and/or Front Door with WAF Policies.
So, the concept is to create at least two custom rules:
The first rule Prevent browsing Existing Directory – and it must include all existing directories of the application:
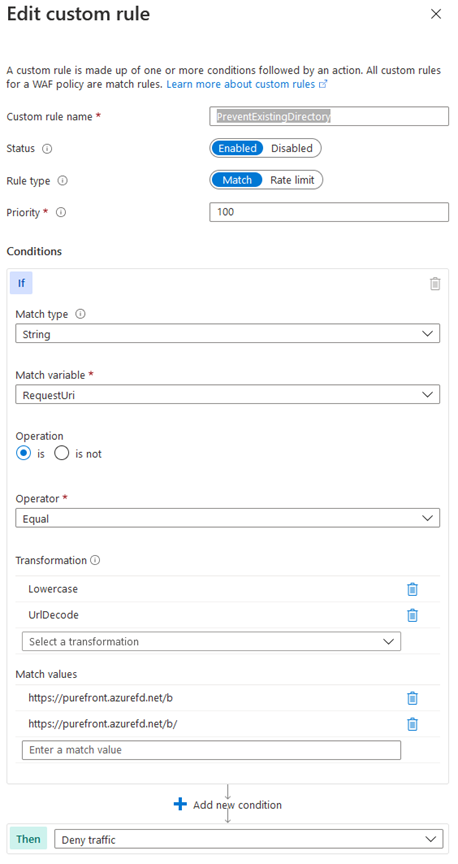
This simply prevents enumerating all directories.
The second rule will allow traffic only to the listed files and directories, but only if the previous does not meet conditions, so files in directories can be browsed.
It can look like:
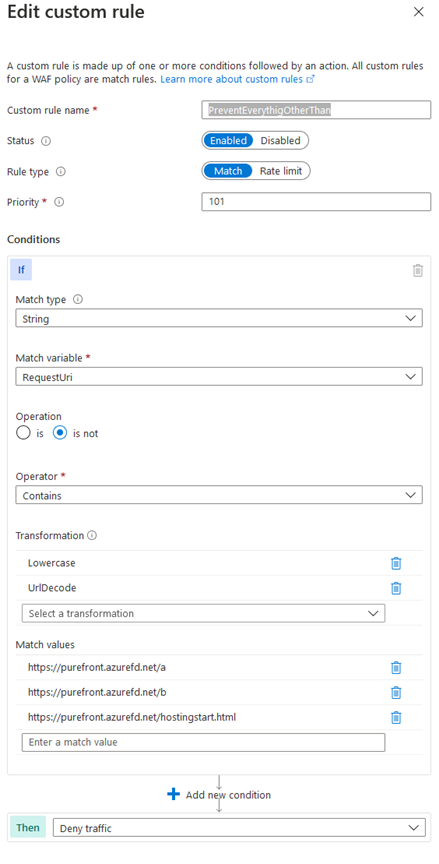
So it is not so easy, but we can use regex also for that.
Another method can be to allow only specific URI based on Regex as a first rule and then as a second rule Deny.
You can also apply your own rules to address the issue, of course.
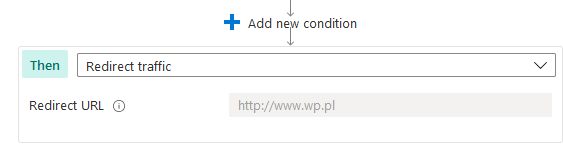
Finally, instead of Deny traffic rule, you can use Redirect traffic: