GCP Logs To Azure Sentinel #1
Create Google Organization:
GCP Account must be a part of the organization – not a “No Organization”, you can create a new one, but it must be an owner internet domain.
You can follow:
https://workspace.google.com/gcpidentity/signup?sku=identitybasic
If you have an organization you can move the existing account to it: https://cloud.google.com/identity/docs/set-up-cloud-identity-admin#migrate-projects-and-billing-accounts-and-set-permissions
- Add billing administrator account principal from organization.
- Add owner account principle from the organization
- You must accept emails.
Activate Terraform API:
Just visit in GCP and activate Cloud Resource Manager API:
https://console.cloud.google.com/apis/library/cloudresourcemanager.googleapis.com
Install Terraform:
curl https://apt.releases.hashicorp.com/gpg | gpg –dearmor > hashicorp.gpg
sudo install -o root -g root -m 644 hashicorp.gpg /etc/apt/trusted.gpg.d/
sudo apt-add-repository “deb [arch=$(dpkg –print-architecture)] https:// apt.releases.hashicorp.com $(lsb_release -cs) main”
sudo apt install terraform
terraform –version
Prapare GCP to Send data to the Azure Sentinel:
mkdir pubsub
cd pubsub/
wget https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/DataConnectors/GCP/Terraform/sentinel_resources_creation/GCPInitialAuthenticationSetup/GCPInitialAuthenticationSetup.tf
export GOOGLE_PROJECT=angelic-hold-403608
gcloud auth application-default login
gcloud config set project angelic-hold-403608
export GOOGLE_APPLICATION_CREDENTIALS=/root/cred.json
where cred.json – are json of credentials downloaded from service account: https://console.cloud.google.com/iam-admin/serviceaccounts
terraform init
terraform apply
In case of error:
Error: Error creating WorkloadIdentityPoolProvider: googleapi: Error 404: Requested entity was not found.
Just retry the terraform apply it is because google API is activated during first time of use.
Create App registration in Azure:
Log in to Azure and Browse to Identity > Applications > App registrations then select New registration.
Only redirect should be composed as:
The 50… value is from Terraform Output.
Create the pub-sub resources:
cd ..
mkdir pubsub2
cd pubsub2
wget https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/DataConnectors/GCP/Terraform/sentinel_resources_creation/GCPAuditLogsSetup/GCPAuditLogsSetup.tf
terraform init
terraform apply
or for entire GCP organization
terraform apply -var=”organization-id={organizationId}”
Create Sentinel Connector:
Open Sentinel you want to send the logs
Open Content Hub
Select Data connectors
Install the following:
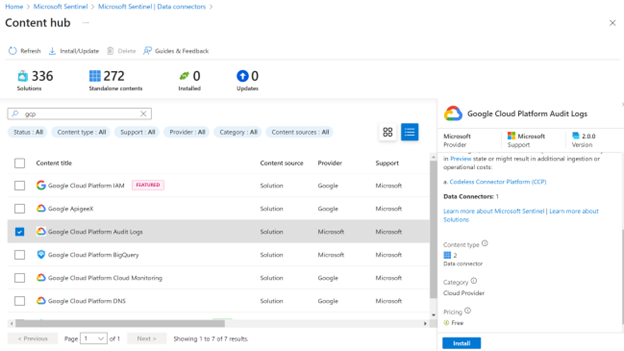
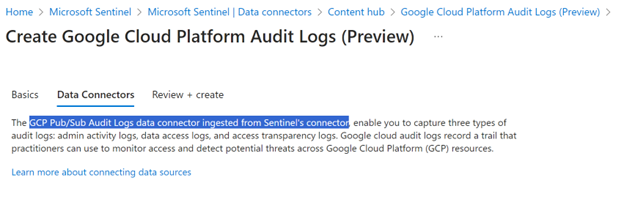
Make sure that data connectors subpage displays “GCP Pub/Sub Audit Logs data connector ingested from Sentinel’s connector”:
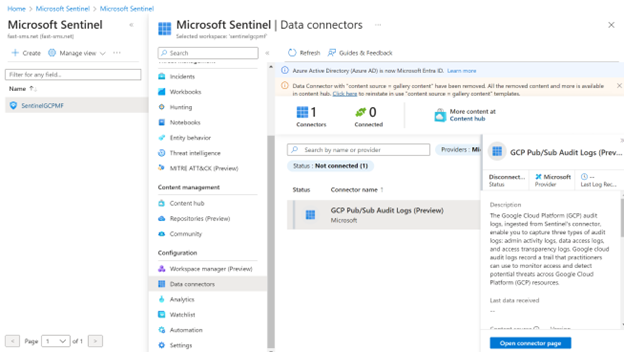
Configure the connector
Open Data Connector click refres select GCP Pub/Sub Audit Logs and Open Connector Page.
Click add new connector and provide details from terraform outputs.
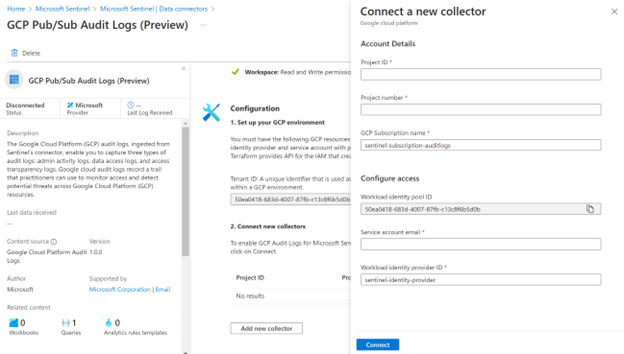
e.g.:
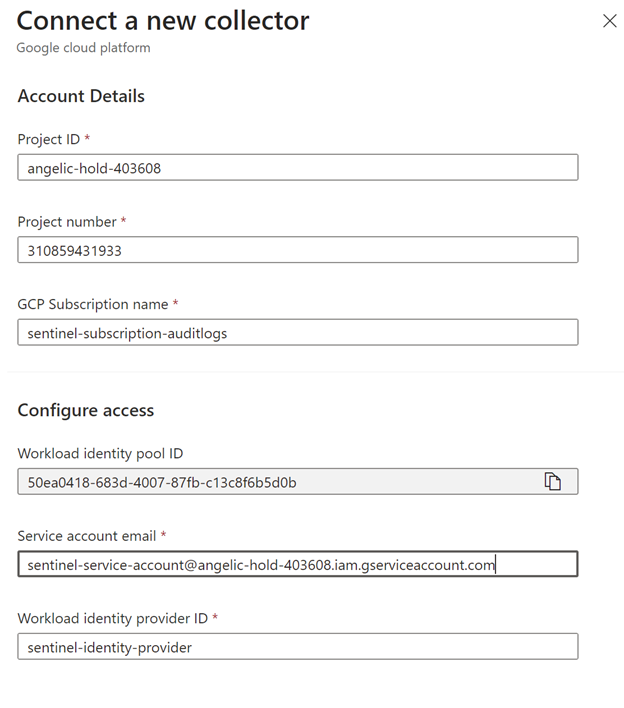
After configuration it should be like:
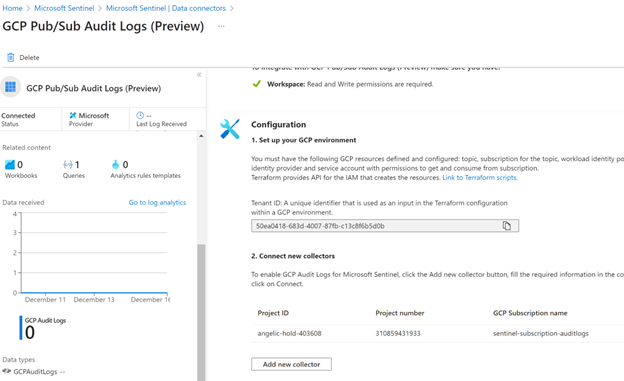
Test de connection
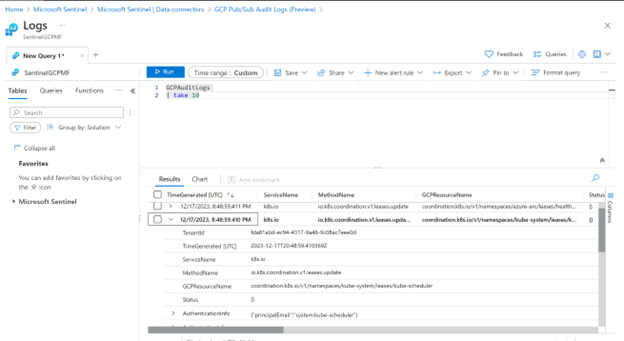
After 1 hour open log analytics and issue KQL query:
GCPAuditLogs
You should see some logs from your GCP projects, like:
More info:
https://learn.microsoft.com/en-us/azure/sentinel/connect-google-cloud-platform
https://cloud.google.com/iam/docs/workload-identity-federation-with-other-clouds#azure
https://registry.terraform.io/providers/hashicorp/google/latest/docs/guides/getting_started
If you want to build your solution you should follow this manual for creating Codeless GCP Connectors: https://learn.microsoft.com/en-us/azure/sentinel/create-codeless-connector
The source code for the connector: https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/Google%20Cloud%20Platform%20Audit%20Logs
The solution is based on a Managed App – so be familiar with: https://rzetelnekursy.pl/azure-managed-application/
Sample Output from Terraform (it should look like):
Plan: 7 to add, 0 to change, 0 to destroy.
Changes to Outputs:
+ An_output_message = “Please copy the following values to Sentinel”
+ GCP_project_id = “angelic-hold-403608”
+ GCP_project_number = “310859431933”
+ Identity_federation_pool_id = “50ea0418683d400787fbc13c8f6b5d0b”
+ Identity_federation_provider_id = “sentinel-identity-provider”
+ Service_account_email = “sentinel-service-account@angelic-hold-403608.iam.gserviceaccount.com”
Do you want to perform these actions?
Terraform will perform the actions described above.
Only ‘yes’ will be accepted to approve.